Vulnerability Assessment: Formulating an effective strategy for vulnerability management

Vulnerability Assessment: Limitations and how to solve them
August 28, 2021
Actionable vulnerability assessment: The ins and outs
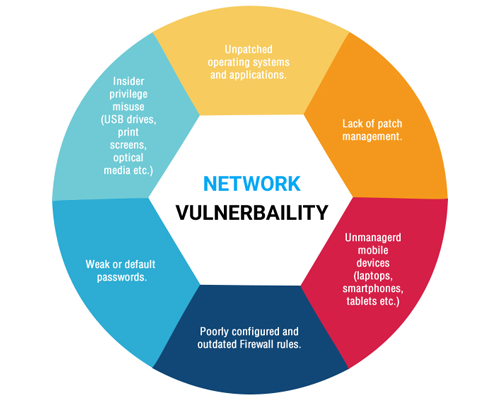
October 12, 2021Vulnerability management is the most widely used method to combat malicious events that may lead to exploitation of vulnerable gaps in a system’s defense. While most organizations adopt a regular vulnerability assessment routine that keeps them updated on the list of known vulnerabilities, the follow-up procedures can take months to complete. This leaves the organization at a serious risk of exposing themselves to unwanted intrusions by unethical actors.
WebSecure, a vulnerability management company, is a leading authority on the topic of network security. It undertakes vulnerability assessment operations and has developed revolutionary measures to tackle unwanted breaches in a network system. With the CVE database reporting over 18,000 vulnerabilities in 2020, excluding vulnerabilities that have not been assigned a CVE identifier, solely conducting a vulnerability assessment is no longer a viable option. It is, therefore, key to identify critical areas and components while developing a robust strategy to safeguard networks from malicious intent.
A panel of professionals at WebSecure have identified key practices that must be adopted by any organization to create a waterproof strategy for vulnerability management. First and foremost, a unified approach to vulnerability assessment must be adopted. A unified approach calls for a combination of numerous assessment methods to ensure that all bases are covered.
Secondly, the strategy must be centered around a continuous assessment schedule to ensure minimal gaps in between scans. Additionally, care must be taken to record all identified vulnerabilities so that an idea can be formulated on the status of the network security.
A vulnerability assessment scan based on CVE data alone is insufficient and may even provoke false responses. Therefore, care must be taken to base every vulnerability scan of a comprehensive database to allow for an in-depth analysis of each vulnerability.
Last but not least, WebSecure experts highly recommend an extensive vulnerability assessment scan. Companies cannot afford to limit their scans to only known vulnerabilities. More than 40 per cent of vulnerabilities don not have CVE identity. One can only imagine the ill-effects of such vulnerabilities being exploited by actors for unethical purposes.
Learning to assess the environment for vulnerabilities is crucial to maintaining a secure system. Even the most effective vulnerability management program is useless if the right strategies are not applied. Thus, WebSecure recommends users to revisit strategies and identify loopholes for an effective vulnerability management strategy.
Also Read :- Vulnerability Assessment: Limitations and how to solve them