The importance of performing network-based vulnerability scans

Is remote working a profound handicap for vulnerability assessment?
November 12, 2021
Remote vulnerability assessment is a must-have for any organization
December 10, 2021The adoption of advanced technology has necessitated the adoption of security systems that can ensure the safeguarding of sensitive data and information used by businesses in their daily operations. One of the most critical component of any security protocol utilized by network systems is vulnerability assessment. Vulnerability assessment forms the basic framework of any security system used to monitor and deal with any liability that exists in the system.
Timely identification and redressal of vulnerabilities that exist within a network system is paramount to running an airtight ship. WebSecure, a vulnerability assessment company knows this all too well. Years of handling vulnerability scans for clients has given the company valuable insight on the most effective methods to deal with vulnerabilities of all kinds. One of the most basic and generic assessment scans employed by organizations is the network-based scan.
What is it?
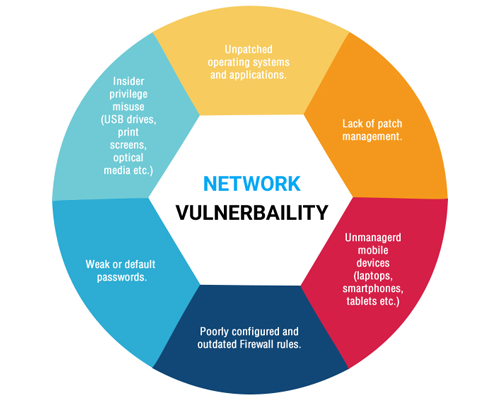
Network-based vulnerability scans focus on identifying any vulnerability that exists in the wired or wireless networks used by a company. These scans help identify possible gaps that could be misappropriated by unethical actors to gain access into the system as well as any unauthorized access points or dubious connections.
How does it work?
According to WebSecure experts, a network-based vulnerability scan is a broad process that encompasses multiple sub-processes. These processes include tasks like:
- Security control check
- Identifying and prioritizing network threats
- Router and Wi-Fi analytics
- Device-level security analytics
- Strengthening network against attacks like Distributed Denial of Service (DDoS)
Why Network-based vulnerability assessment?
WebSecure’s team of experts explain that network systems bear witness to some of the most incessant probing by unscrupulous actors who wish to gain access to protected data. Unauthorized devices and remote access servers, insecure networks of business partners and unknown parameter points present in networks provide possible ingress points for unwanted players.
Running a network-based vulnerability scan helps mitigate these vulnerabilities and identify new ones. As always, network scans need to be run on a regular basis to gain deeper insight and gleam actionable data points that can strengthen network security.
Also Read:- Actionable vulnerability assessment: The ins and outs