December 16, 2021
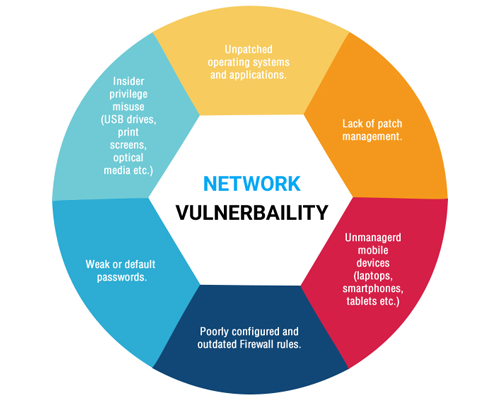
If you believe that human actors pose the greatest risk to cyber security, the following sentences will surely shake your core beliefs. Granted, that till date […]
December 10, 2021
The increased risks associated with remote working is proving to be a serious cause of concern. Unsurprisingly, the work-from-home environment is proving to be an appealing […]
November 24, 2021
The adoption of advanced technology has necessitated the adoption of security systems that can ensure the safeguarding of sensitive data and information used by businesses in […]
November 12, 2021
Change is the only constant. Adapting to it is a critical skill to stay ahead of the times. This holds relevancy in the digital world where […]
October 12, 2021
In the world of vulnerability assessment, there is a lot of data to go around after every scan. Every data is potentially a goldmine of information […]
September 16, 2021
Vulnerability management is the most widely used method to combat malicious events that may lead to exploitation of vulnerable gaps in a system’s defense. While most […]
August 28, 2021
As much as vulnerability assessment has become a crucial aspect of cybersecurity in today’s day and age, it is not the perfect solution. Vulnerability assessment is […]
August 4, 2021
‘A little knowledge is a dangerous thing’ goes the famous proverb. The saying could not have been more eloquently put to describe vulnerability assessment (VA) management […]
July 13, 2021
Data security and privacy have become a pertinent issue for business and organizations worldwide. Despite employing advanced security measures to thwart unauthorized access, companies are increasingly […]