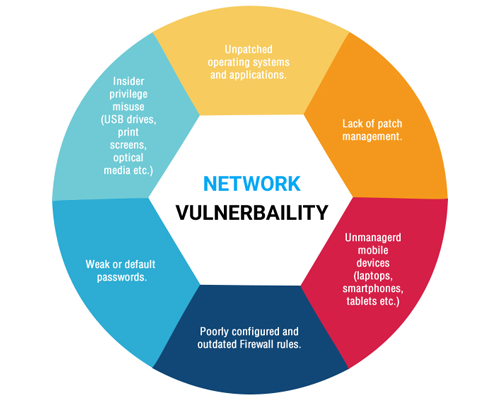
Is Automated Vulnerability Assessment superior to Manual Assessment?

Vulnerability Assessment Checklist: What Companies Need To Know
June 10, 2021
Cloud computing and vulnerability assessment scans
July 5, 2021A majority of everyday processes and applications have all undergone a certain degree of automation. This is certainly true when it comes to digital networks and cybersecurity. Intelligent programs and applications that are designed to think and address issues are available everywhere. This however raises the all-important question – is automatic vulnerability assessment programs better than manual assessment?
WebSecure, a vulnerability assessment company, has considerable experience in this field and proceeds to expound on the subject for a better understanding. Automated and manual vulnerability assessments are two types of security tools usually employed by businesses to secure their network systems.
The automated approach to vulnerability testing employs a tool or a program to detect vulnerabilities in a system. The program can be customized to look for certain types of vulnerabilities or loopholes which can be used by unethical players to gain access to private data. However, this is where the automated vulnerability assessment has an inherent weakness. After it discovers vulnerabilities, how the program exploits them is unpredictable. Will it exploit it and if it does, up to which extent? Will it be able to exploit the loopholes in order to provide better feedback to the operator?
These are a few drawbacks faced by the operators when using automated vulnerability assessment. Our experts at WebSecure say that while the automation certainly simplifies the checks and steps to be performed by a human operator, the focus is on the vulnerabilities of the system as a whole. Specific loopholes are usually missed by such sweeps and even if they are detected, their exploitation will require a manual intervention to assess the severity of the exposure.
There is no single way to tackle rising cybersecurity breaches and data leaks. Automated and manual vulnerability assessment checks will have to be performed together in order to get the best of both worlds. Vulnerability assessment professionals at WebSecure recommend that every vulnerability assessment performed by businesses should include automated and manual checks in equal measure. A combination of the two methods will help eradicate much of the loopholes in a system and address cybersecurity issues more efficiently.