Cloud computing and vulnerability assessment scans

Is Automated Vulnerability Assessment superior to Manual Assessment?
June 22, 2021
Vulnerability Assessment with a Modern Twist
July 13, 2021The advent of cloud computing and its widespread adoption by the global business community has introduced a paradigm shift in the data industry. Cloud computing is no doubt versatile and adaptive to the varied demands of businesses and companies. However, its introduction has also opened a new can of worms.
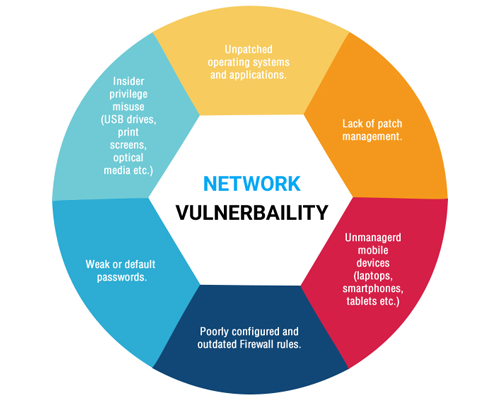
A full-proof system as such is yet to see the light of day. Cloud computing is no different. It certainly has its weakness that can be used by unethical players to access private data. Security professionals at WebSecure say that it does not matter what services a company uses; vulnerability assessment scans will always be required. While the techniques implemented differ, the end goal remains the same – detecting vulnerabilities in the system.
Vulnerability assessment companies like WebSecure have to constantly adapt to stay ahead of the pack when it comes to system security. Cloud security poses a significant challenge, unlike traditional systems. The hybrid environment mix of services like Software-as-a-service (SaaS) and public cloud deployments renders traditional methods obsolete. Therefore, innovative solutions have to be devised to tackle such issues.
WebSecure experts disclosed that the trick to performing an effective vulnerability assessment for cloud systems lay in understanding the IT and cloud security. A complete understanding of the IT system and security measures in place will prove valuable in identifying the shortcomings of the system. A vulnerability assessment scan is only effective as long as a thorough knowledge of the system in question is had.
Recent times have revealed that cloud computing and storages are not invulnerable to unscrupulous acts. Private data and information on the cloud have been accessed through unethical means which hardly showcases cloud services in good light. Such instances are not a 100 per cent avoidable but their occurrence can be minimized by smart implementation of vulnerability assessment scans. Scans should be conducted on a regular basis and uncovered weaknesses address with utmost haste.
Also Read:- Is Automated Vulnerability Assessment superior to Manual Assessment?