Why Enterprises Should Look For Experts To Carry Out Vulnerability Management Processes

Important Factors That Companies Must Consider During Vulnerability Management
November 5, 2020
Why organizations cannot overlook the importance of vulnerability scanning
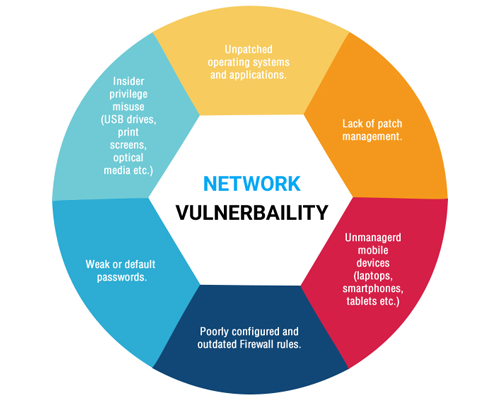
December 4, 2020Vulnerability management has become an integral part of the companies’ IT systems. It not only helps in the detection of security concerns across various systems of an organization but also fixes multiple problems, while minimalizing the vulnerability-related risks in the long run. Many companies are obtaining desired results from useful vulnerability management techniques.
Assessment of vulnerability is one of the most important processes of vulnerability management. It is carried out differently, depending upon the characteristics of an organization. It helps in the detection of weaknesses and offers a detailed remedy to iron out flaws.
Vulnerability assessment is able to protect the systems from external sources. It ensures the elimination of all the loopholes across the security paradigm. Thus, it requires a comprehensive understanding of the subject to conduct assessment with great precision. This is where companies like WebSecure are automating this process to take the lead in offering holistic vulnerability management solutions. The firm identifies, evaluates and reports vulnerabilities for enterprises that aim to iron out flaws by hiring the experts of this segment. It helps in the identification of several systems running on a network, such as laptops, virtual and physical servers, firewalls, etc.
Read More: How vulnerability management plays a vital role in mitigating possible threats
Depending on the type of business, the scope of vulnerability management is quite vast. It also showcases how vulnerability assessment is just a part of the greater vulnerability management plan, rather than an independent process. Similarly, vulnerability scanning may take the lead in vulnerability management solutions, but it is only used to probe systems for different attributes, including operating system, open portals, installed software, user accounts, etc.
The entire process of vulnerability management is transparent but result oriented. It is arguably the best possible way of protecting security systems from external threats that are increasing on a daily basis.