Vulnerability Assessment Or Penetration Test: Is One Better Than the Other?

Risk-Based Vulnerability Management: The Next Step In Vulnerability Assessment
May 20, 2021
Vulnerability Assessment Checklist: What Companies Need To Know
June 10, 2021In today’s digitally-driven world, new technologies are being introduced every day. Added to this is a plethora of technical jargons which would confuse even professionals. This has led to certain words being used to address subjects which are contrary to the word’s intended meaning.
Penetration Test is one of those terms which is often used in the wrong context. Owing to its similarity with Vulnerability Assessment, with regard to operation, it is mistakenly used to describe techniques employed under the former. WebSecure experts say that such mistakes could prove costly in the long run as companies are in the dark about the exact procedures they have employed to secure their networks.
According to experts at WebSecure, Vulnerability Assessment and Penetration Test are similar yet very dissimilar in many ways. Misunderstanding their differences can leave a massive hole in cybersecurity defenses.
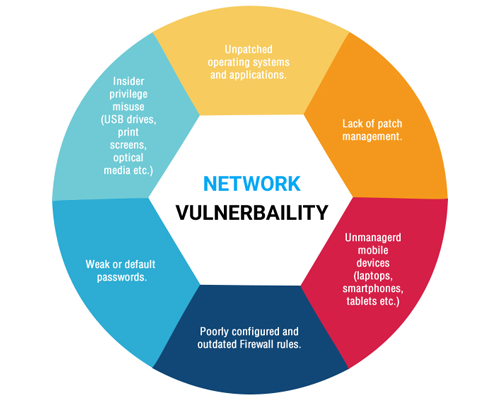
Vulnerability Assessment
Vulnerability Assessment identifies vulnerabilities in the system and makes a list of the ones that could be used by unethical actors to gain access. It is used to evaluate the susceptibility of a network to different vulnerabilities. It provides a baseline of what vulnerabilities exist in the system.
Penetration Test
A Penetration Test is similar to Vulnerability Assessment in the sense that it identifies vulnerabilities. It goes a step further and attempts to use these vulnerabilities for gaining access to the system. Its sole purpose is to determine whether the identified vulnerability is genuine. More often than not, a penetration task follows a vulnerability assessment check to ensure fool-proof security.
WebSecure’s panel of security experts expound on the differences between the two through the coverage they provide. While Vulnerability Assessment specializes in uncovering multiple weaknesses in the network, Penetration Test focuses on utilizing a known vulnerability to enter the system.
In order to ensure fool-proof security systems, a mix of both methods must be employed. One complements the other and will enhance the protection level offered by existing cybersecurity protocols and ensure that crucial data remains out of reach of unidentified players.