Modeling Cybersecurity – An Innovative Countermeasure In The Digital World

WebSecure thwarts external threats to safeguard firms with result-oriented solutions
March 31, 2021
Are Vulnerability Assessment Scans Enough To Keep Unethical Actors At Bay?
April 29, 2021According to experts at WebSecure, out of a thousand vulnerabilities, only a few are exploited and it is usually a handful of vulnerabilities that are accountable for a majority of snags.
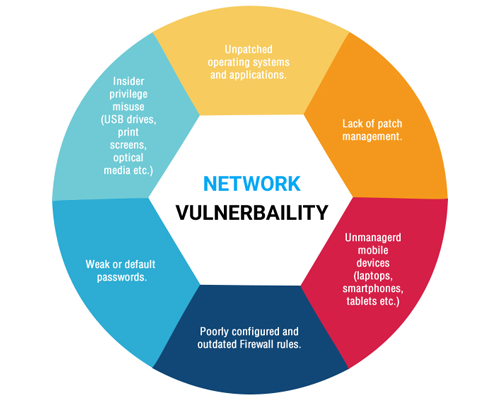
The widespread use of digital technology in today’s world has necessitated the application of Vulnerability Assessment. While it is commendable to see more businesses get more tech-savvy and avail such services, a clearer understanding of Vulnerability Assessment will prove beneficial in the long run.
A simple account of a system’s vulnerabilities and the application of preventive measures is not enough anymore. Unscrupulous actors are always coming up with imaginative ways to gain access to confidential files and sensitive information. To tackle such underhanded means, quality vulnerability assessment plays a crucial role.
Identifying and classifying vulnerabilities according to their severity and occurrence can be the most effective counter. This can be done in two ways – categorizing loopholes from the system’s point of view or taking the intruder’s point of view and identifying the possible strategies.
Regardless of the approach, the end goal is the same – to define the most effective steps that will protect the concerned system. Defending all known vulnerabilities may sound good on paper but is pointless and a waste of resources. According to experts at WebSecure, out of a thousand vulnerabilities, only a few are exploited and it is usually a handful of vulnerabilities that are accountable for a majority of snags.
Data provided by Recorded Future, a cybersecurity company, reveals that it is unrealistic to assume that intruders will go for random vulnerabilities to worm their way in. It is also equally unrealistic to assume that they know their targets like the back of their hand.
What this means is that there is no one-stop solution. However, WebSecure experts agree that although no two incursions are alike, there is always a similarity in tactics, techniques and procedures (TTPs). If one is to plan an effective defense, it is worthwhile to go through known TTPs.
The importance of Threat Modelling cannot be stressed enough. Vulnerability Assessment companies like WebSecure recognize this and are continuously improving their modelling procedures.
As the entire world is almost digitally connected, private data and records will be more susceptible to unethical actors. The need of the hour is potent counter-measures against such breaches.
Also Read :- WebSecure thwarts external threats to safeguard firms with result-oriented solutions